







Stronger Defence Against Advanced Cyber Attacks

Hybrid Structure
Advanced Defence Technologies
Live Analysis
7/24 Up to Date
Automated Protection
Including advanced technologies; TINA GOVERNMENT PROTECTION, analysis internet traffic simultaneously on the fly; without any human interference automatically detects and intercepts cyber attacks, isolates malicious clients (if preferred), logs all these interceptions on unlimited cloud storage and reports cyber event summaries of local/overall network and worldwide TINA statistics on monthly bases.
TECHNOLOGIES








TINA GOV is HYBRID:
Includes Local (on device) Technologies
and
Central (cloud) Technologies
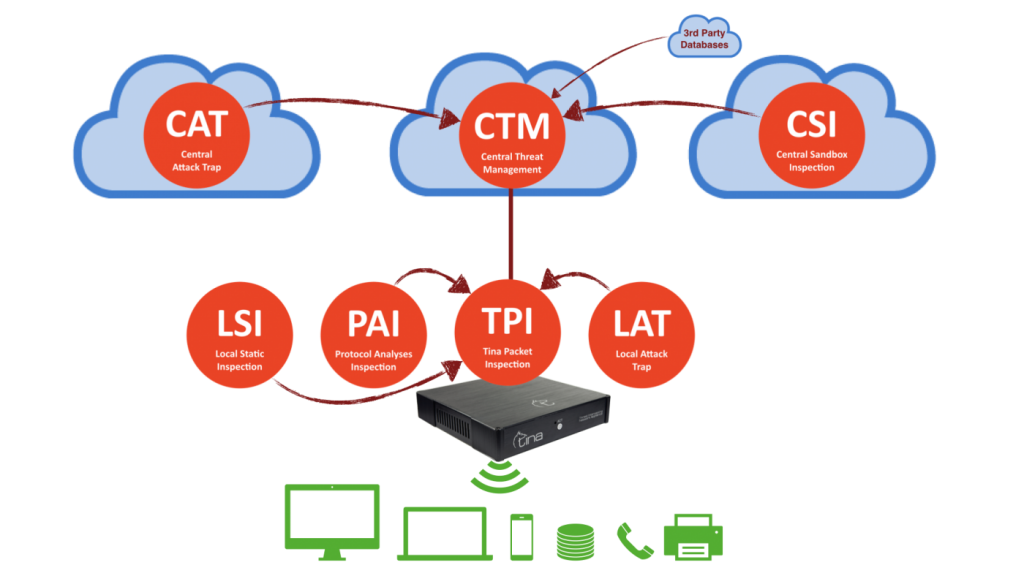
Local Technologies





TINA GOV detects local threats with it’s TPI (TINA Packet Inspection) technology by; Tracking and Applying Threat Databases, Live Traffic Analysis, Attacker Call-Back Traffic Analysis.
In addition to TPI Instant technologies, LAT – Honeypot technology enables Hyperactive Threat Inspection, and PAI – Protocol Analysis Investigator technology enables Prevention of Attack On Initial Phase and Prevention of Attacker On The Job.
TINA GOV also detects local threats with multi-way analysis and direct connection to CTM.
CTM Update runs 7/24 database and software updates automatically.
Cyber events; statistics, detections and interceptions made are reported on CTM Management.
LSI Static Sandbox technologies enables fast, automated and supervised analysis of suspicious Internet files with local+cloud integrated sandbox analysis.
Central Technologies




TINA GOV detects local threats with multi-way analysis and direct connection to CTM.
CTM Update runs 7/24 database and software updates automatically.
Cyber events; statistics, detections and interceptions made are reported on CTM Management.
CAT Global Detection technologies are set along worldwide to detect global threats. CAT (Central Attack Trap) technologies collects attack data while EDI (Enhanced Domain Intelligence) technologies are gathering pre-intelligence worldwide cyber security sources.
CSI Static Sandbox technologies enables automated and supervised analysis of suspicious files, links and supports with fast sandbox analysis.
With CTM Multidevice you can run multiple devices on same dashboard and take reports separately.
CTM Management and CTM SIEM enables controlling of your account from a centre and sharing logs to a SIEM.
TINA Baits enables use of decoy files as both honeypot and data leakage alarming system.
TINA GOV is AUTOMATED:
Provides assistance and enables higher controlled defence, by itself.
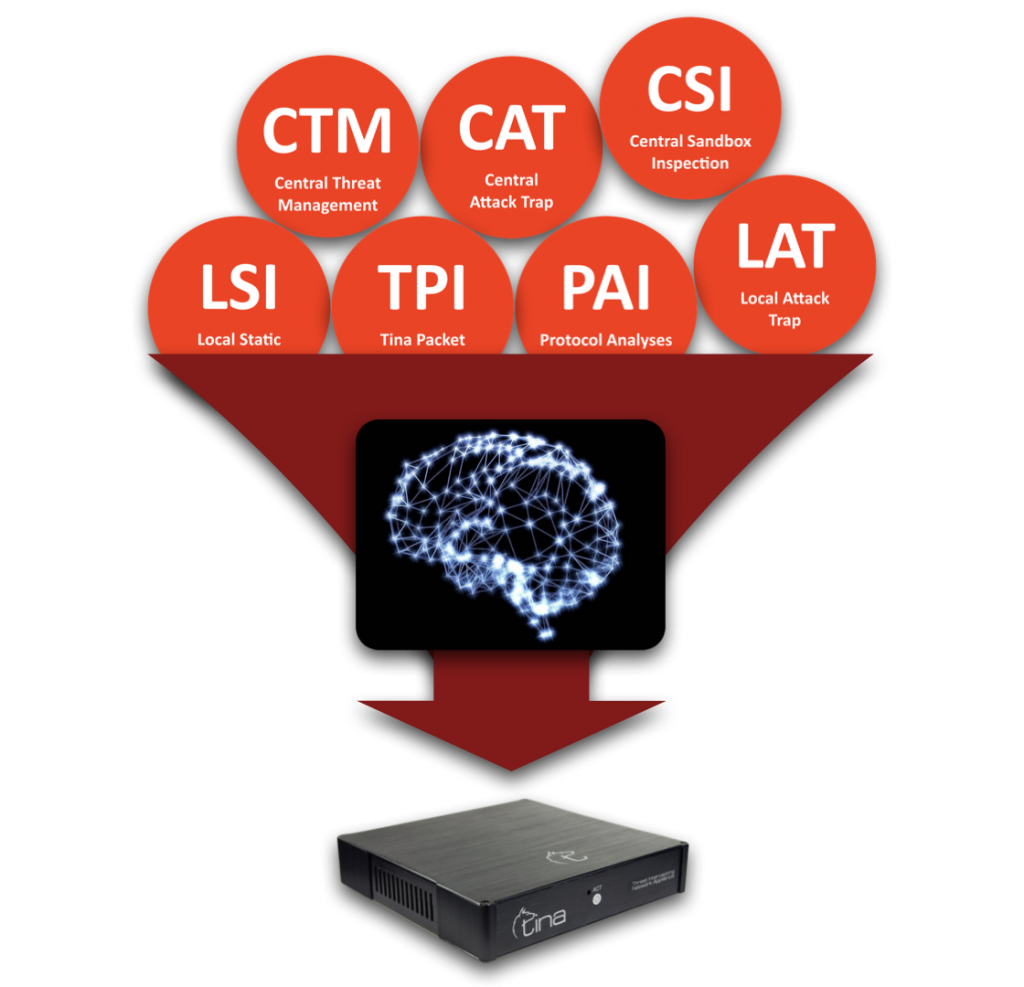
TINA GOVERNMENT
Enables top level defence against both known, unforeseen or unknown attacks, even if they are successful.
COMPARED WITH OTHER MODELS
|
YEARLY SUBSCRIPTION PRICE* |
Starting from 11.200 € |
Starting from 18.700 € |
Starting from 13.900 € |
|
SIZING |
|||
| Small Business | 0 – 50 User | 0 – 50 User | 0 – 150 User |
| Medium Business | 0 – 250 User | 0 – 250 User | 0 – 750 User |
| Enterprise | 250+ User | 250+ User | 750+ User |
| Multi-location / Branch / Multidevice | Additional devices available** | Additional devices available** | Additional devices available** |
|
LOCAL (ON-DEVICE) TECHNOLOGY LICENSES |
|||
| Update License | Included | Included | Included |
| Management License (about CTM) | Included | Included | Included |
| TPI Analysis License (about TPI) | Included | Included | Included |
| Honeypot License (about LAT) | Included | Included | Included |
| PAI License (about PAI) | Included | Included | Included |
|
CENTRAL TECHNOLOGY LICENSES |
|||
| CAT Detection License (about CAT) | Included | Included | Included |
| Static Sandbox License (about LSI) | Included | Included | Included |
| Multidevice License | Included | Included | Included |
| SIEM Interaction License | – Optional – | Included | Included |
| Dynamic Sandbox License (about CSI) | – | Included | – |
| Bait License | – | Included | Included |
*Pricing table shows bare prices, valid across European Union and may be subject to change during final purchase.
Initial subscription to a model includes 1 year license subscription and free device rental.
** Additional devices are subject to a fee.
For detailed information about TINA technologies subject to licensing, please visit TECHNOLOGIES page.
SIZING LIMITATIONS
Small Business |
Medium Business |
Enterprise |
|
| Hardware Model | TINA 2nd Generation | TINA 2nd Generation | TINA 2nd Generation
/ TINA 3rd Generation |
| User Allowance | 0 – 50 | 0 – 250 | 250 + |
| User Limit | *** | *** | none |
| Internet Bandwidth Limit | *** | *** | 10 Gbps Traffic / 1 Gbps Analysis |
| Device Limit | *** | *** | 15.000 |
| Rate Limit | *** | *** | none |
*** To be declared on sales offer.
HARDWARE SPECIFICATIONS
TINA 2nd Generation |
|
|---|---|
| DEVICE LIMIT (MAXIMUM CONCURRENT) | 0 – 5.000 |
| RUNNING MODE | Bridge |
| RACK MOUNT | Optional |
| FAILSAFE FEATURE | Electronic & Mechanical |
| FRONT PANEL | 1 x Power button 1 x Power light, 1 x Sata light |
| BACK PANEL | 1 x Reset button 1 x Power light, 1 x Sata light 1 x 12V/5A DC in 4 x RJ-45 LAN input |
| NETWORK CARD | 4 Port Intel Gigabit Card |
| STORAGE | 1 x 16 GB SSD mSATA HDD |
| POWER ADAPTER | Input : 100-240V (AC) Output : 12V/5A (DC) |
| POWER CONSUMPTION | 35 Watt |
| DIMENSIONS | 19.0 x 19.5 x 3.8 cm |
| NET WEIGHT | 0.95 kg |
| OPERATING CONDITIONS | Temperature: 5 to 40°C (41 to 104°F)Humidity: 20% to 90% RH |
| STORING CONDITIONS | Temperature: 5 to 70°C (41 to 158°F)Humidity: 5% to 95% RH |
| PACKAGE CONTENTS | 1 x TINA Main Unit 1 x License Certificate 1 x Power Adaptor 1 x Power Cable 1 x Ethernet Cable 1 x User Guide 1 x Warranty Certificate |

